Get industry-leading certification training and pioneer a career in IT and Cybersecurity.
$197.00 / month for 10 months
Our course bundle makes it super easy for you to step into your career by giving you everything you need to get started:
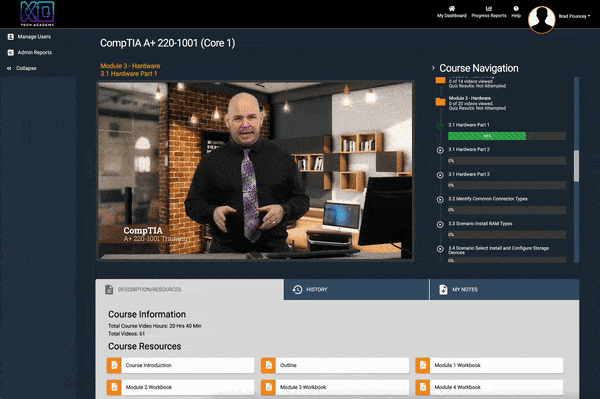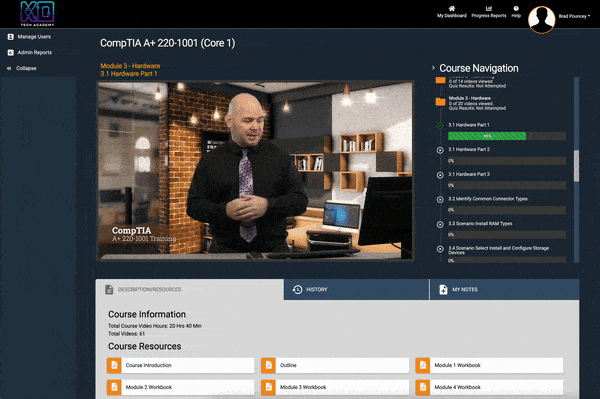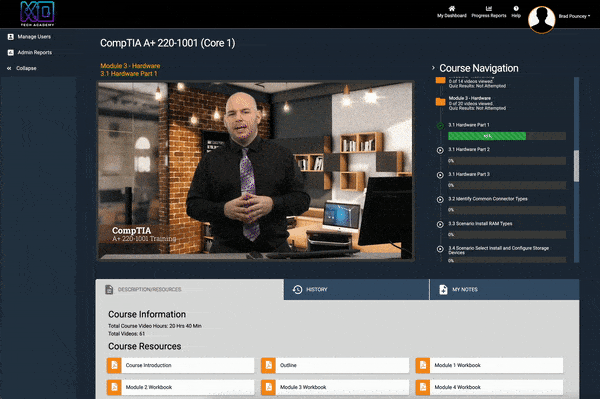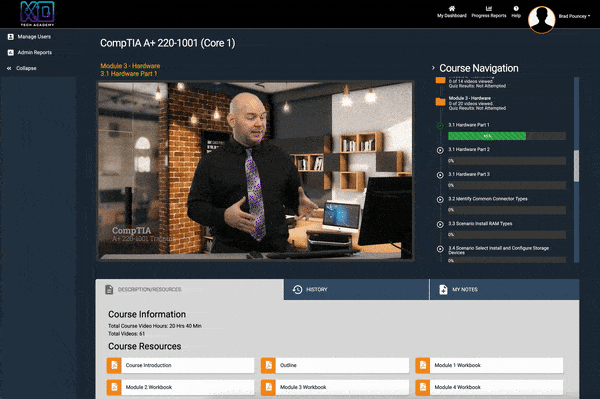
You’ll begin your journey in our online training platform, where you’ll get everything you need to ace your first few industry certifications - and access for a year to continue education!
As you approach testing day, you’ll have interactive learning tools and comprehensive workbooks with pages of notes to review to ensure you pass with flying colors.

During your certification training & your IT job search, you’ll have access to our online student & alumni group, where you can connect with folks to pair study or find new opportunities out in the field.
Unlock the knowledge to jumpstart your new IT career today!









Course 1
The CompTIA IT Fundamentals course and exam focuses on the knowledge and skills required to identify and explain the basics of computing, IT infrastructure, software development, and database use.
Course 2
The CompTIA A+ certified professionals support today’s core technologies from security to cloud to data management and more. CompTIA A+ is the industry standard for launching IT careers into today’s digital world.
Supporting Multiple Drive Types and Memory
Memory Types
RAM Types
Memory Modules
DIMM and SO-DIMM Technologies
Parity and ECC RAM
Memory Compatibility Issues
Discussing System Memory Installation
Install and Configure Mass Storage Devices
Storage Adapters and Cables
Solid State Drives
Guidelines for Installing Mass Storage Devices
Discussing Mass Storage Device Installation and Configuration
Install and Configure Removable Storage
Discussing Removable Storage Device Installation and Configuration
Configure RAID
RAID Configuration Options
Discussing RAID Configuration
Troubleshoot Storage Devices
Boot Failures
Discussing Storage Device Troubleshooting
Wired Networks
Common Ethernet Network Implementations
Taps and Mirrors
Discussing Wired Networks
Network Hardware Devices
Switches
Power Over Ethernet
Discussing Network Hardware Devices
Wireless Networks
Access Points and Wireless Network Modes
Discussing Wireless Networks
Internet Connection Types
Wireless Internet Service Providers WISP
Discussing Internet Connection Types
Network Configuration Concepts
The TCIP-IP Protocol Suite
Internet Protocol and IP Addressing
Public and Private IP Addresses
IPv6
Discussing Network Configuration Concepts
Network Services
DNS
Dynamic and Static IP Configurations
DNS Records MX and A
Web Servers and HTTP-HTTPS
Discussing Network Services
Configuring and Troubleshooting Networks
Network Connections in Windows
Install and Configure SOHO Networks
Configure SOHO Network Security
Firewalls
Port Fowarding and Port Triggering
Windows Firewall
Network Security and Embedded Appliances
Configure Remote Access
Discussing Remote Access Configuration
Troubleshoot Network Connections
IP Configuration Issues
Routing Issues
Discussing Network Connection Troubleshooting
Configure Client-Side Virtualization
Hypervisors
Processor Support and Resource Requirements
Virtual Networks
Client-Side Virtualization
Cloud Computing Concepts
Internal and External Shared Resources
Cloud Service Options
Virtual Desktops
Software-Defined Networking (SDN)
Discussing Cloud Computing Concepts
Use Laptop Features
Expansion Options
Discussing Laptop Features
Install and Configure Laptop Hardware
Discussing Laptop Hardware Installation and Configuration
Troubleshoot Common Laptop Issues
Discussing Troubleshooting Common laptop Issues
Syncing and Setup of Mobile Devices
Connect and Configure Mobile Devices
Configure Mobile Device Network Connectivity
Mobile VPN Configuration
Email Configuration Options
Discussing Mobile Device Network Connectivity Configuration
Support Mobile Apps
Discussing Mobile App Support
All Things Printing
Discussing Laser Printer Maintenance
Maintain Inkjet Printers
Discussing Inkjet Printer Maintenance
Maintain Impact, Thermal, and 3D Printers
Discussing Impact, Thermal, and 3D Printer Maintenance
Install and Configure Printers
Discussing Printer Installation and Configuration
Troubleshoot Print Device Issues
Install and Configure Imaging Devices
Discussing Device Installation and Configuration
Threats and Security Measures
Logical Security Concepts
Encryption
PKI and Certificates
Execution Control
NAC
Discussing Logical Security Concepts
Threats and Vulnerabilities
Types of Password Attacks
Discussing Threats and Vulnerabilities
Physical Security Controls
Discussing Physical Security Measures
Policies to Protect Data
Implement Security Best Practices
Guidelines for Implementing Security Best Practices
Discussing Security Best Practices Implementation
Implement Data Protection Policies
ACLs and Directory Permissions
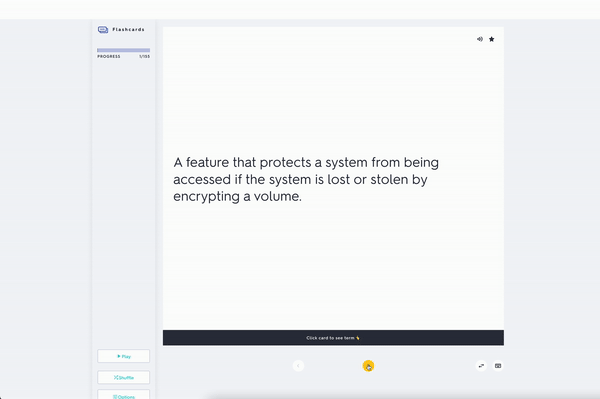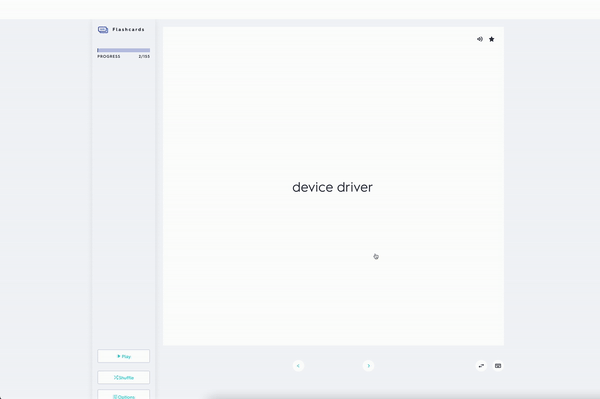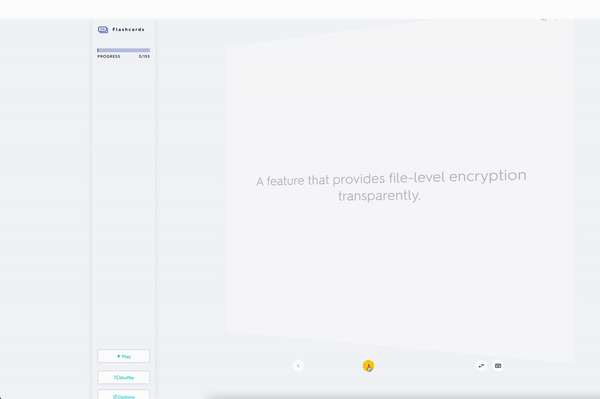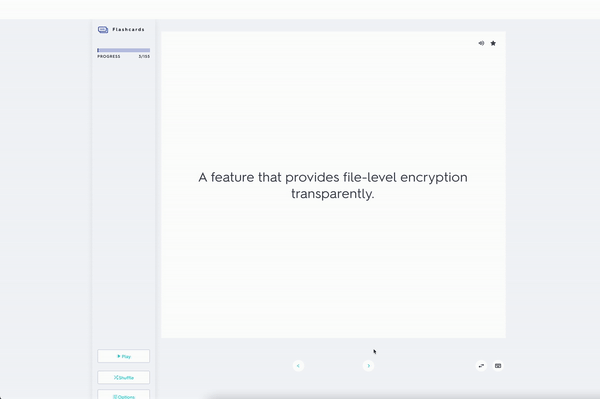
Full Disk Encryption
Guidelines for Implementing Data Protection Policies
Discussing Data Protection Policies
Protect Data During Incident Response
Discussing Data Protection During Incident Response
Prevent Malware and Security Threats
Detect, Remove, and Prevent Malware
Trojan Horses and Spyware
Sources of Malware Infection
Best Practices for Malware Removal
Discussing Detecting, Removing, and Preventing Malware Infections
Troubleshoot Common Workstation Security Issues
Discussing Troubleshoot Common Workstation Security Issues
Supporting and Troubleshooting Mobile Devices
Secure Mobile Devices
IOT Internet of Things
Discussing Mobile Device Security
Troubleshoot Mobile Device Issues
Mobile Device Security Troubleshooting
Discussing Troubleshooting Mobile Devices
Implementing Operational Procedures
Environmental Impacts and Controls
Discussing Environmental Impact and Controls
Create and Maintain Documentation
Discussing Documentation Creation and Maintenance
Use Basic Change Management Best Practices
Discussing Change Management Best Practices
Implement Disaster Prevention and Recovery Methods
Discussing Implement Disaster Prevention and Recovery Methods
Basic Scripting Concepts
Discussing Scripting
Professionalism and Communication
Discussing Professionalism and Communication Skills
Course 3
The CompTIA Network+ course and exam is a mid-level certification for network technicians. It’s designed to test the competency of a mid-level network technician and their ability to support and configure TCP/IP clients through network design, cabling, hardware setup, configuration, installation, support, and troubleshooting.
Course 4
Implement Secure Network Designs
Implement Secure Switching and Routing
Various Types of Network Attacks Demo
Implement Secure Wireless Infrastructure
Implement Load Balancers
Module Summary
Implement Firewalls and Proxy Servers
Implement Network Security Monitoring
Summarize the Use of SIEM
Module Summary
Implement Secure Network Operations Protocols
Implement Secure Application Protocols
Implement Secure Remote Access Protocols
Module Summary
Implement Secure Firmware
Implement Endpoint Security
Endpoint Protection Demo
Explain Embedded System Security Implications
Module Summary
Implement Mobile Device Management
Implement Secure Mobile Device Connections
Module Summary
Analyze Indicators of Application Attacks
Analyze Indicators of Web Application Attacks
Summarize Secure Coding Practices
Implement Secure Script Environments
Summarize Deployment and Automation Concepts
Module Summary
Summarize Secure Cloud and Virtualization Services
Apply Cloud Security Solutions
Summarize Infrastructure as Code Concepts
Module Summary
Explain Privacy and Data Sensitivity Concepts
Explain Privacy and Data Protection Controls
Module Summary
Summarize Incident Response Procedures
Utilize Appropriate Data Sources for Incident Response
Apply Mitigation Controls
Module Summary
Explain Key Aspects of Digital Forensics Documentation
Explain Key Aspects of Digital Forensics Evidence Acquisition
Module Summary
Explain Risk Management Processes and Concepts
Explain Business Impact Analysis Concepts
Module Summary
Implement Redundancy Strategies
Implement Backup Strategies
Implement Cyber Security Resiliency Strategies
Module Summary
Explain the Importance of Physical Site Controls
Explain the Importance of Physical Host Security Controls
Module Summary
Conclusion and General Exam Tips
Course 5
This CCNA training is considered associate-level Cisco training, which means it is designed for junior network administrators. this 200-301 CCNA course is valuable for new IT professionals with at least a year of experience with networks and experienced network administrators looking to validate their Cisco skills.
After taking this course, the exam tests a candidate’s knowledge and skills related to network fundamentals, network access, IP connectivity, IP services, security fundamentals, and automation and programmability.
What will you learn?
CCNA exam objectives and topics include the following:
Course 6
Course 7
The Microsoft 70-698 course focuses on how to install Windows 10 with a minimal amount of administrative effort. Preparation, the process, activation, and troubleshooting will be covered in this IT training session. You will also learn how to perform an in-place upgrade from Windows 8.1 to Windows 10, configure hardware devices, manage device drivers, and perform post-install configuration.
Course 8
An Ethical Hacker certification is a much-sought-after security certification offered by EC-Council. The topics in this course cover a broad range of concepts and techniques and will provide you with a solid foundation to pursue advanced cybersecurity studies.
Information Security Overview
Hacking Concepts
Ethical Hacking Concepts
Penetration Testing
Penetration Testing Part 2
Activity - Performing a Static Code Review
Ports
TCP Flags and Handshakes
TCP Scan Types
Other Scanning Techniques
Scanner Output and Reports
Vulnerability Research
Review
Metasploit
Metasploit Search
Metasploit Exploits and Payloads
Metasploit Meterpreter
Metasploit Connectivity
Metasploit Impersonation and Migration
Netcat
Pivoting
Netcat Relays
Metasploit Post Exploitation Modules
Common Operating System Exploits
Hacking Windows
Hacking Linux
Network Service Exploits
Password Attacks
Dictionary Attack
Brute Force Attack
Password Spraying
Rainbow Tables
Network Service Password Attacks
Password Cracking Tools
Online Password Cracking Sites
Windows Password Cracking
Linux Password Cracking
Other Methods for Obtaining Passwords
Keylogging
Spyware
Rootkits
Buffer Overflows
Privilege Escalation
Hiding Files
Alternate Data Streams
Steganography
Creating and Maintaining Remote Access
Hiding Evidence
Covering Tracks in Windows
Covering Tracks in Linux
System Hacking Counter-Measures
System Hacking Penetration Testing
Review
Intro to Malware
Virus Overview
Virus Types
Self-Hiding Viruses
Worms
Trojans
Trojan Types
RATS
Ransomware
Botnets
Covert Channel Trojans
Banking Trojans
Rootkits
Other Malware
Malware Makers
Dropper and Stage Creation
Exploit Kits
Malware Detection
Malware Detection Part 2
Malware Analysis
Malware Reverse Engineering
Malware Countermeasures
Malware Penetration Testing
Review
Sniffing Concepts
Types of Sniffing
Sniffing Protocols
Sniffing Tools
ARP
ARP Spoofing
MITM
MAC Attacks
MAC Spoofing
DHCP Attacks
Name Resolution Poisoning
VLAN Hopping
Sniffing Counter Measures
Sniffing Penetration Testing
Review
Social Engineering Concepts
Social Engineering Techniques
Social Engineering Examples
Social Engineering Tools
Social Media
Identity Theft
Insider Threats
Social Engineering Countermeasures
Social Engineering Penetration Testing
Review
DoS-DDoS Concepts
Volumetric Attacks
Fragmentation Attacks
State Exhaustion Attacks
Application Layer Attacks
Protocol Attacks
Other Attacks
Botnets
DoS-DDoS Attack Tools
DoS-DDoS Countermeasures
Dos Penetration Testing
Review
Mobile Platform Overview
Mobile Device Vulnerabilities
Mobile Device Attacks
IT-OT Convergence
ICS
SCADA
DCS
RTU
PLC
Addition OT Components
Digital Certificates
Digital Signatures
Hashing
Email Encryption
Network Communication Encryption
Course 9
The CompTIA Cybersecurity Analyst (CySA+) certification verifies that successful candidates have the knowledge and skills required to configure and use threat detection tools, perform data analysis and interpret the results to identify vulnerabilities, threats and risks to an organization, with the end goal of securing and protecting applications and systems within an organization.
Get an entire year to study the course materials, and use the practice labs to learn everything you need to know for certification.
Study comprehensive workbooks with hundreds of pages of notes covering every video topic to help you learn easily.
Enjoy detailed lessons taught by experienced certified IT instructors who guide you every step of the way.
Discover interactive study materials in every course including flash cards and matching games to help you master every subject.
Learn exactly what you need to prepare yourself for the most powerful, in-demand, IT industry certifications in existence.
Join us in our free, private Facebook community to connect with other students who are starting new careers just like you.
As soon as you purchase! After we receive payment, you’ll be sent a voucher code via email from KO Tech Academy with the subject line “You received a new voucher code”. It typically takes a couple hours for processing on our end, so don’t panic if you don’t receive your voucher code immediately. Once you’ve received your voucher code, follow the instructions in the email to setup your account and access your Learning Management System (LMS) Dashboard.
You get to work! Once you’ve created your account and accessed your dashboard, you’re free to start taking your courses and accessing all of your materials. Remember you have full access for an entire year!
There is no restriction on what order you take your courses in, but we definitely recommend taking the courses in order. They’re designed to build on each other as you progress and learn more and more.
For IT & Cybersecurity, we recommend the following order:

The Online Training You Need to Launch Your Tech Career
You can receive 25% off of any course purchase.
Email any form of military or official, professional identification to support@kotechacademy.com for verification.